The Emergence of Open and Organized Pro-Government Cyber Attacks in the Middle East: The Case of the Syrian Electronic Army
Authored by Helmi Noman.
Noman is a Senior Researcher at the Citizen Lab, Munk School of Global Affairs (University of Toronto), and a Research Affiliate at the Berkman Center for Internet and Society, Harvard University.
Crossposted from the InfoWar Monitor.
Introduction
Since the beginning of the popular uprisings and protests in the Middle East and North Africa, events in the region have been characterized by increased contestation in cyberspace among regime sympathizers, governments, and opposition movements. One component of this contestation is the tendency among governments and networks of citizens supportive of the state to use offensive computer network attacks. Such tactics are supplements to legal, regulatory, and other controls, and technical forms of Internet censorship.
For example, a group known as the Iranian Cyber Army has defaced Twitter and Iranian opposition websites. Also, Tunisian political activists and Yemeni oppositional websites have both accused their government security organizations of launching attacks on their sites in an attempt to silence their message and deny access to their content.
In this report, we document the activities of the Syrian Electronic Army, which appears to be a case of an open and organized pro-government computer attack group that is actively targeting political opposition and Western websites. Our aim is to assess to what extent we can find evidence of Syrian government assistance for the attack groups, and what the significance of the attacks themselves are for civil society and cyberspace contestation.
Overview
Syria has become the first Arab country to have a public Internet Army hosted on its national networks to openly launch cyber attacks on its enemies. The intensity and scope of the Syrian Electronic Army’s activities signal an interesting development in the Syrian pro-regime Internet arena: In addition to being one of the most repressive Internet censors in the region, the local media, some of which is government-run is apparently supporting the Army’s orchestrated aggressive efforts to attack, by means of website defacements and comment spamming, political opposition and Western websites.
The Syrian Electronic Army claims on its website that it was founded by a team of young Syrian enthusiasts who did not want to stay passive “towards the fabrication of facts on the events in Syria.” Information Warfare Monitor (IWM) research found that the group has a connection with the Syrian Computer Society, which was headed in the 1990s by the current Syrian President Bashar al-Assad before he became president.
The Army has been attacking and defacing Syrian oppositional and “hostile Western news” websites. However, IWM found that some of the targeted Western websites are actually not news websites but rather non-political commercial websites. Although Facebook has been disabling the Army’s Facebook pages, the Army has been creating alternative pages and has been actively spamming popular and political Facebook pages with highly repetitive and orchestrated pro-regime comments.
About the Syrian Electronic Army
The Syrian Electronic Army, also known as Syrian Electronic Soldiers, claimed on its “about” web page when it was launched in the second week of May 2011 that it was not an official entity, but rather a group of young people who love their country and have decided to fight back electronically against those who have attacked Syrian websites and those who are hostile to Syria. The Army replaced its “about” web page with a new one on May 27, 2011. The Army removed from the new page the reference to it not being an official entity and said it was founded by a team of young Syrian enthusiasts to fight those who use the Internet and especially Facebook to “spread hatred” and “destabilize the security” in Syria. References to it not being an official entity were still found on other pages on the site as footnotes.1 Information Warfare Monitor (IWM) research found out that the domain name for the Army’s website (syrian-es.com) was registered on May 5, 2011 by the Syrian Computer Society (SCS), an organization that was headed by the Syrian President Bashar al-Assad in 1995 before he assumed the Presidency.
The SCS was founded in 1989 by President al-Assad’s brother the late Bassel Al-Assad, who was also its first president. According to its website, “The SCS aims at introducing IT into various Syrian economic [sic]. It also aims to diffuse informatics culture by means of organizing conferences, symposia, seminars, lectures, and exhibitions, in addition to producing TV programs and issuing pamphlets concerning IT.”
Technical investigation shows that the Army’s official website is hosted by SCS-NET, the ISP arm of SCS.
The following is the Army’s domain name registration record as retrieved from domain name WHOIS database:
syrian-es.com
Registrant:
NET, SCS-
Beirut Street
Damascus, SY 13365
SYDomain Name: SYRIAN-ES.COM
Administrative Contact , Technical Contact :
NET, SCS-
[email protected]
Beirut Street
Damascus, SY 13365
SY
Phone: +96311446677636Record expires on 05-May-2012
Record created on 05-May-2011
Database last updated on 05-May-2011Domain servers in listed order:
NS1.SCS-NET.ORG 213.178.225.4
NS2.SCS-NET.ORG 213.178.225.3
First Appearance
The Syrian Electronic Army first emerged on Facebook in April 2011, days after the anti-regime protests escalated in the country. The first Facebook page (http://facebook.com/syrian.es) was disabled by Facebook shortly after being created. Almost immediately the Army created a new page (http://facebook.com/syrian.es1), but again, it was disabled by Facebook. Since then, the group has been creating new Facebook pages every time one is disabled. By May 23, 2011, the group had created 14 pages. The Army created 4 pages between May 23 and 25, all of which were disabled almost immediately.
The Army then released a statement criticizing Facebook for disabling the Army’s pages and vowed to continue creating new Facebook pages. Earlier in May, the Syrian government-run al-Thawar newspaper accused Facebook’s administration of conspiring against the Syrian people and said Facebook had double standards because it shut down pages belonging to the Syrian Electronic Army without any justification or prior notice, yet it restored a pro-revolution Facebook page after it was hacked and deleted by pro-regime activists.
On May 27, the Army released the screenshot of the alleged message that Facebook has been sending them when removing a page (See Figure 1 below). The text in the message reads:
Your Page [name of page in Arabic] has been removed for violating our Terms of Use. A Facebook Page is a distinct presence used solely for business or promotional purposes. Among other things, Pages that are hateful, threatening, or obscene are not allowed. We also take down Pages that attack an individual or group, or that are set up by an unauthorized individual. If your Page was removed for any of the above reasons, it will not be reinstated. Continued misuse of Facebook’s features could result in the permanent loss of your account.
If you need further assistance with this issue, please visit http://www.facebook.com/help/contact.php?show_form=page_disabled.The Facebook Team.
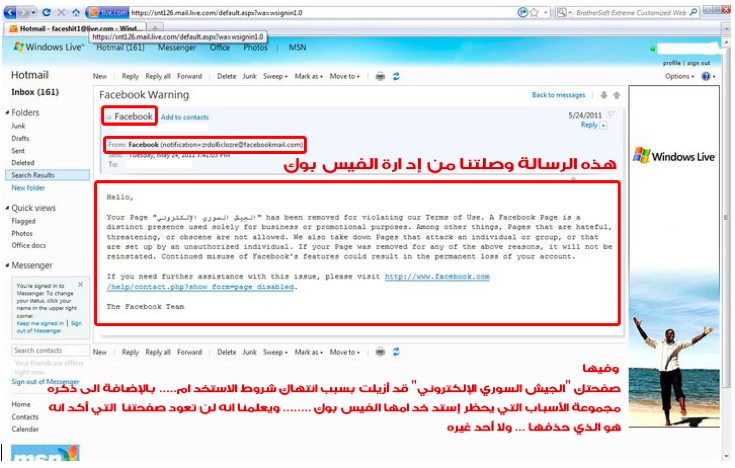
Figure 1: Screenshot of an alleged Facebook message sent to the Syrian Electronic Army notifying them of their page removal.
Tracking the Army’s Facebook pages has been easy because the URL naming convention used by the Army has been predictable incrementing the number at the end of the URL, and because the Army has been publicizing the new URLs on its official website. More recently, however, they adjusted their naming scheme and at the time of writing the Army’s Facebook Page is at https://www.facebook.com/ses.syrian.
Interestingly, however, the group has maintained an unpublicized Facebook page (http://on.fb.me/kOiZoJ). It appears that the Army is attempting to avoid Facebook’s attention. This technique seems to have been successful; Facebook has not targeted the page even though the page hosts the same content as those that have been disabled. The unpublicized page had more than 11,684 members as of May 26, 2011.
Earlier in May, the Army started the Twitter account @syriansolider, but on May 27 it moved to @syriansoldier1 because it lost the first one under unclear circumstances. Also in May, the Army created a YouTube channel http://youtube.com/user/syrianes1 that contains mostly video clips showing the targeted websites before and after the attacks and highlights the reason why each site was attacked as well as the messages the attackers left on each site. Syrian national songs are played as background music on these clips. The channel also hosts a few clips showing pro-regime demonstrations in cities around the world.
Syrian Electronic Army Activities
The Army’s online activities can be divided into three key areas: 1) Defacement attacks against Syrian opposition websites; 2) defacement attacks against Western websites; and 3) spamming popular Facebook pages with pro-regime comments.
1) Defacement attacks against Syrian opposition websites
The Army has been attacking opposition websites run by groups or individuals. The first Facebook pages made software available to their members that can be used to launch distributed-denial-of-service (DDoS) attacks. The founder of the Army, who was not named, was quoted by Syrian news website Tartous Today as saying that the group uses a “widely available program” to launch attacks on hostile websites, and that he had contacted the program developer who promised to send him an enhanced customized version of that program. The founder did not mention the name of the program.
On May 17, 2011, the Army claimed to have attacked over 50 websites in coordination with Arab and Syrian hackers. It added that none of the targeted websites had been destroyed and that all the Army does is “places a temporary page that presents our words and the voice of the truth.” (See Figure 2 below.)
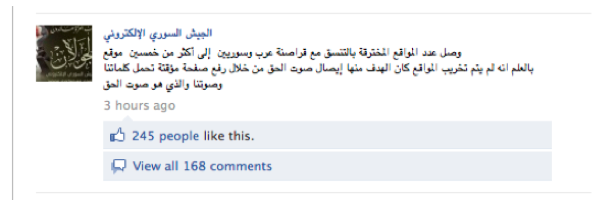
Figure 2: Syrian Electronic Army Facebook page announces that over 50 websites have been attacked, and that it did not destroy content of any of the websites.
IWM can confirm that a number of websites have indeed been defaced and that pro-Syrian regime messages and photos of a Syrian flag and/or Syrian President Bashar al-Assad were left on these websites. In some cases the defaced pages were removed the same day but in other cases the messages remained for days.
For example, the Army has claimed responsibility for hacking the web forum http://news.syriaforums.net because “it spreads fabricated video clips of anti-regime protests in Syria.” (See Figure 3 below.)
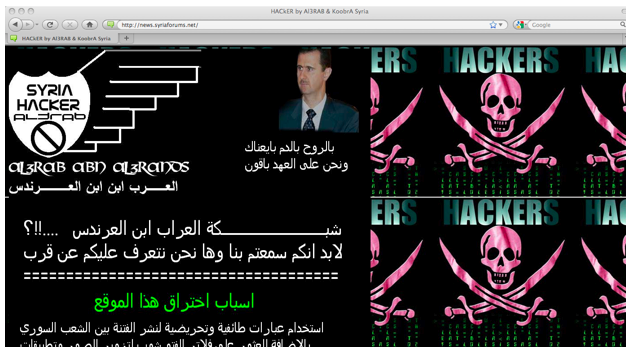
Figure 3: Screenshot of defaced website http://news.syriaforums.net
Another example is the website of popular Syrian singer Asalah Nasri (who currently lives in Egypt), which was defaced just a few days after newspapers reported that she supported the revolution against the Syrian regime and that she rejected an invitation to go to Syria to sing in support of President Bashar al-Assad. The Arabic text left on her defaced website (http://queenasalah.com) described her as a traitor, and asked her to remember that the late Syrian President Hafiz al-Assad had at some point paid for her medical treatment. Ironically, the attackers also mentioned that Syrian hackers have supported her in the past by hacking a website of an Egyptian singer who allegedly criticized the Syrian singer. (See Figure 4 below.)
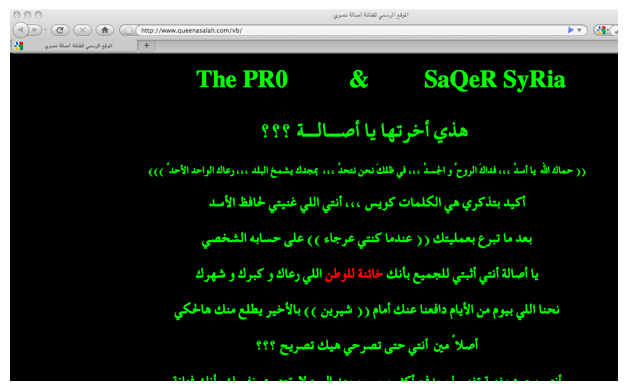
Figure 4: Screenshot of defaced website of Syrian Singer Asalah Nasri http://www.queenasalah.com
2) Defacement attacks against Western websites
The Army has claimed responsibility for defacement attacks against a number of Western websites including http://leamingtonspatowncouncil.gov.uk, the website of the Royal Leamington Spa Town Council. The attackers compromised the website and replaced the original content with the following text (See Figure 5 below):
Sorry, we do not want to destroy your official website, but the British Government actions and attitudes against Syria and its interfering in the Syrian internal affairs forced us to step forward and break through your website
We, the Syrian, don’t harm anybody, but if you dare to interfere in the Syrian Internal Affairs we are able to put appropriate limits
STOP to interfere in the Syrian Internal Affairs
Leave us alone
[email protected]
Dr.Hanan Noura
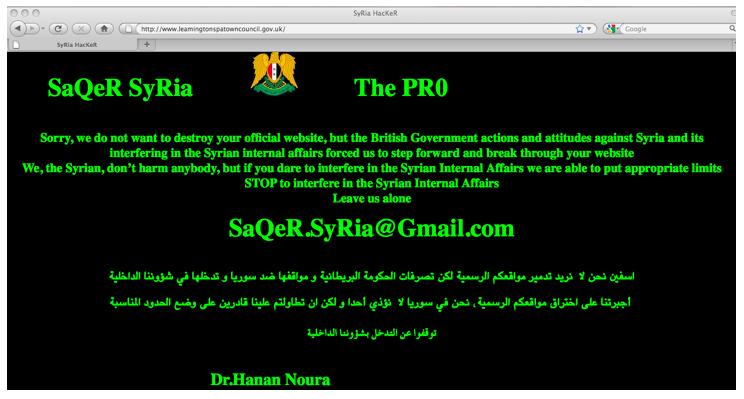
Figure 5: Screenshot of defaced website of Royal Leamington Spa Town Council (http://www.leamingtonspatowncouncil.gov.uk)
Interestingly however, several of the targeted western websites do not seem to be politically relevant despite the fact that the Army claimed they are news websites that spread anti-regime news. In some cases, the Army said they were targeted “as a revenge from the foreign countries behind them.”
For example, the Army claimed responsibility for defacing the Italian websites http://bluereef.it (See Figure 6 below), http://windcam-news.it/usato/s, (See Figure 7 below) and http://aguide2italy.com (See Figure 8 below).
In these cases, the Army said that it attacked the websites because “they disseminated fabricated news about Syria”. (See Figure 9 below.) The IWM have verified that these websites have indeed been defaced and that pro-Syrian regime messages were left on these websites. However, these sites are online shops and a tourism guide, and they do not seem to have media stories about Syria.
Further, the Army claimed responsibility for defacing the “British” website http://kl7uk.com “as a revenge from the British government for its hostile stand on Syria” (See Figure 10 below).
It is not clear whether the websites were attacked by mistake due to lack of understanding of Italian or English, or simply because they were soft targets. Another possibility is that the Army targets websites that are perceived to be popular as a means to disseminate pre-Syrian regime messages to users of these websites.
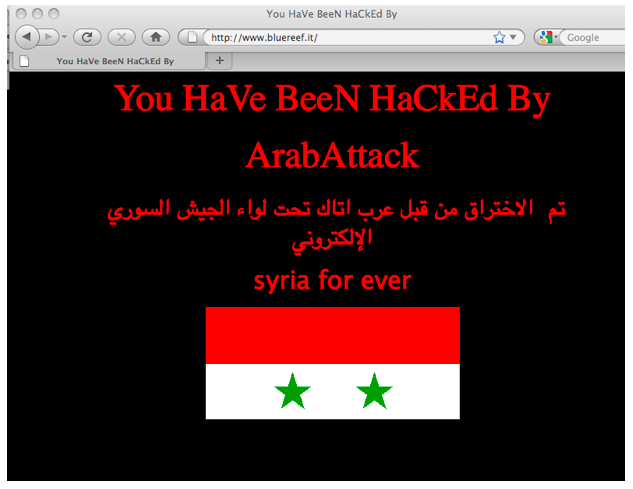
Figure 6: Screenshot of defaced website http://www.bluereef.it.
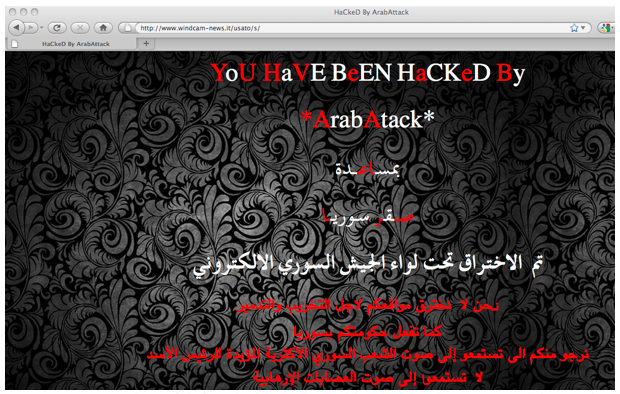
Figure 7: Screenshot of defaced website http://www.windcam-news.it/usato/s.
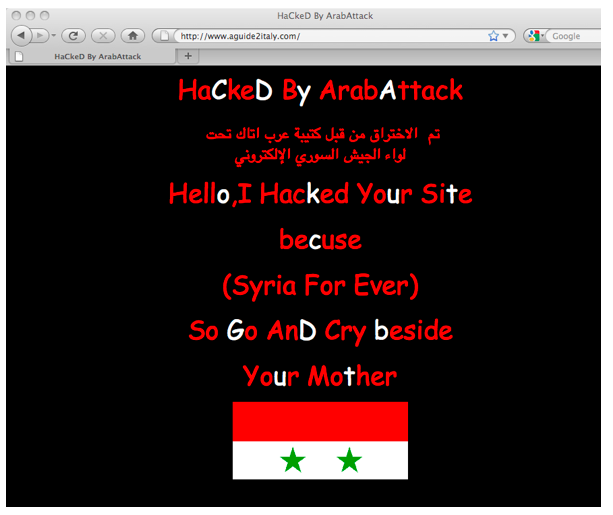
Figure 8: Screenshot of defaced website http://www.aguide2italy.com.
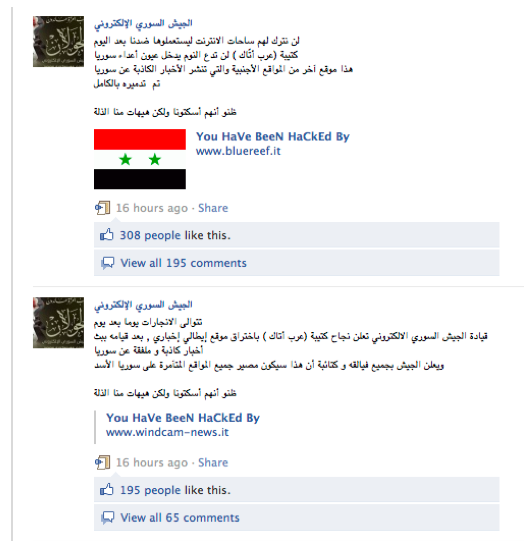
Figure 9: Syrian Electronic Army Facebook page claims responsibility for hacking the websites http://www.bluereef.it and http://www.windcam-news.it because “they spread fabricated news about Syria.”
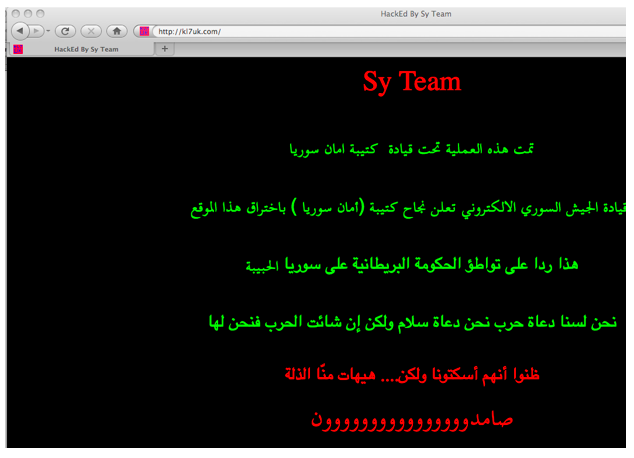
Figure 10: Syrian Electronic Army claims responsibility for hacking the “British” website http://kl7uk.com as a revenge against the British government for its hostile stand on Syria
3) Spamming popular Facebook pages with pro-regime comments
The Army has been organizing massive spam attacks on popular and political Facebook pages. In these attacks, the Syrian regime supporters post on a pre-selected Facebook page highly repetitive comments under multiple posts in a short period of time (one or two hours). Several pages have been targeted by this type of attack including pages of the European Parliament, European Union, White House, U.S. Department of State, U.S. President Barack Obama, French President Nicolas Sarkozy, Oprah Winfrey, Human Rights Watch, al-Jazeera TV channel, al-Arabia TV channel, and religious scholar Sheikh Yusuf Al Qaradawi.
The Army gives different reasons for why each page was chosen. (See Figures 11 to 15 below.) For example, Oprah Winfrey’s page was targeted as a means to influence American public opinion; TV stations’ pages were targeted to influence their coverage of the events in Syria; the European Union page was targeted to protest the EU’s stand on the regime; and Sheikh Al Qaradawi’s website was targeted because he showed support to the revolution in Syria.
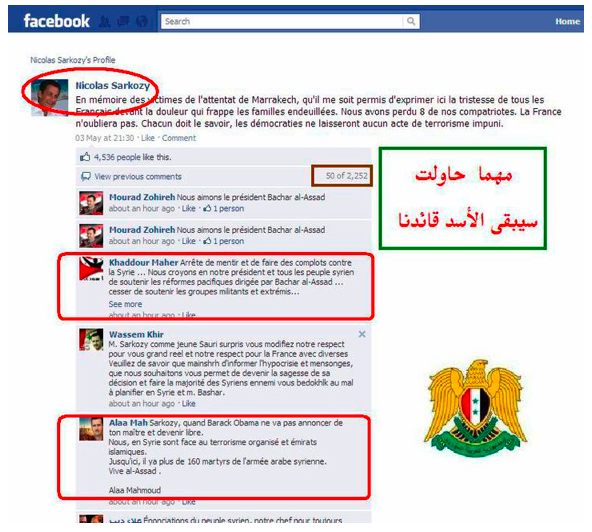
Figure 11: Syrian Electronic Army documents its “virtual demonstration” on French President Nicolas Sarkozy.
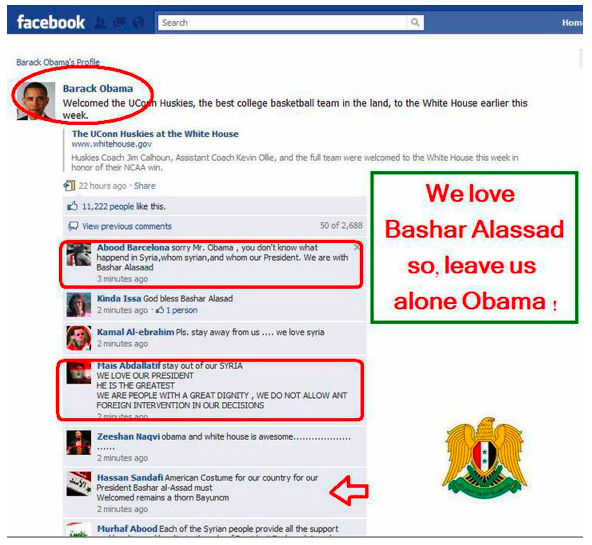
Figure 12: Syrian Electronic Army documents its “virtual demonstration” on US President Barack Obama
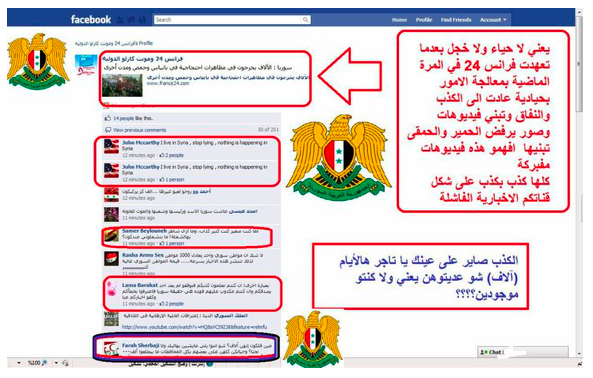
Figure 13: Syrian Electronic Army documents its protests on French news site France24 and says that the anti-regime protests video clips broadcast by France 24 are fabricated.
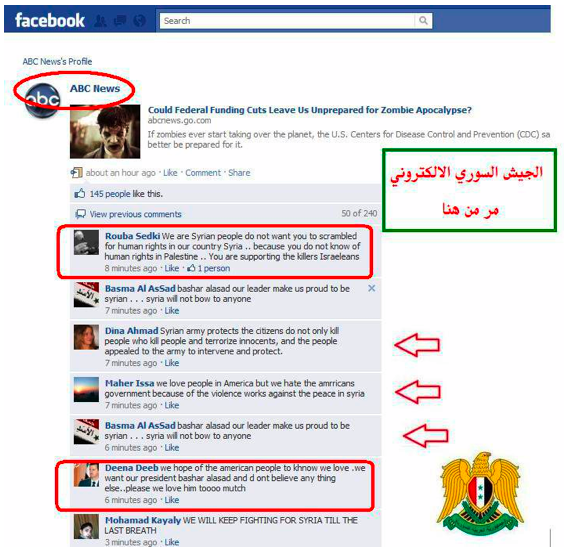
Figure 14: Syrian Electronic Army documents its protests on ABC News Facebook page.
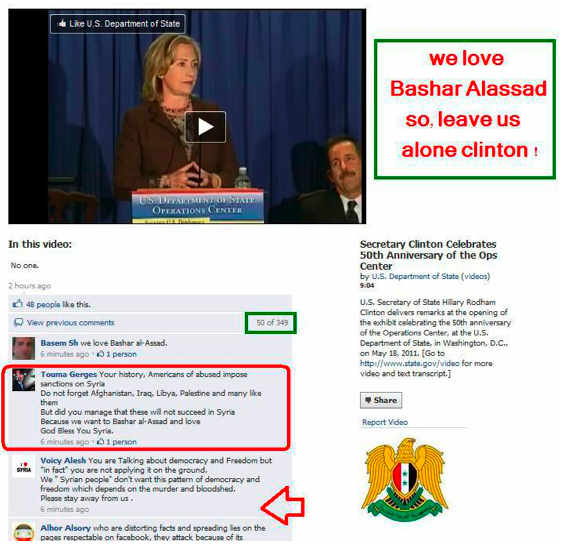
Figure 15: Syrian Electronic Army documents its protests on U.S. Department of State Facebook page.
Other Activities
The Army has conducted opinion polls and asked its Page members to vote for what type of websites they prefer to see attacked. The vast majority voted for American websites, followed by British websites. Few voted for Italian websites. (See Figure 16 below.)
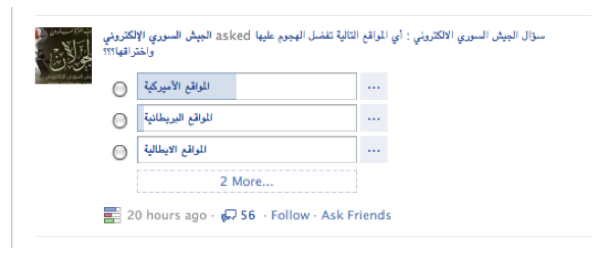
Figure 16: Screenshot of an opinion poll conducted by the Syrian Electronic Army Facebook page.
The Army often asks its “soldiers” to get ready for the next attack and specifies the timeframe (See Figure 17 below). The Facebook page usually does not immediately announce what website has been hacked. Instead, the page announces that the Army will “break good news soon,” perhaps to build excitement among its fans and to solicit comments, which are often in the hundreds (See Figure 18 below). In some cases, the Army posts links to YouTube clips that “document successful hacking attacks on websites.” (See Figure 19 below.)
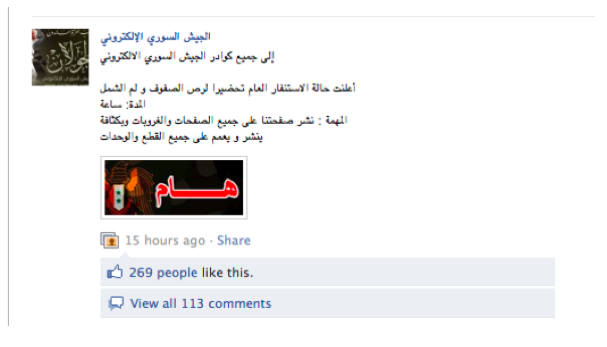
Figure 17: Facebook page asks the “soldiers” to get ready within 30 minutes for the next attack.
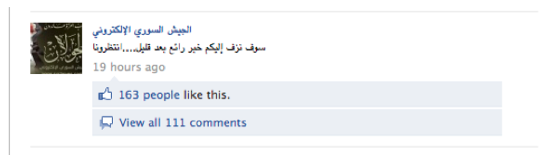
Figure 18: In this screenshot, the administrator of the Syrian Electronic Army Facebook page says: “Good news [of a successful attack] will be announced soon. Stay tuned.”
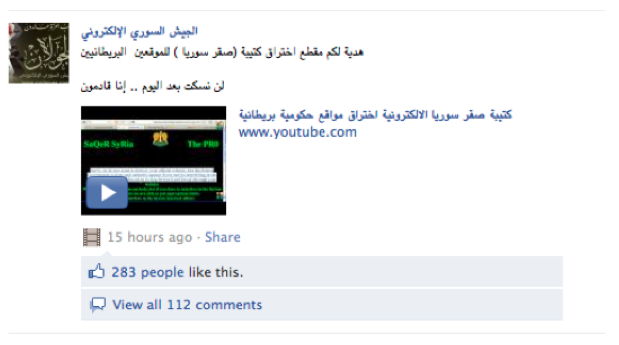
Figure 19: Syrian Electronic Army posts to Facebook a YouTube clip about hacking British government websites.
The Army and the Media
The Army and its activities have received ample celebratory attention from local Syrian media. Articles supportive of the Army and critical of Facebook for disabling the Army’s pages appeared in the websites of the Ministry of Information, government-run al-Thawra newspaper, government-run al-Wehda newspaper, and Syria Now. Army members have been interviewed by the state TV channel and a radio station. Army members remained anonymous and the founder of the Army was introduced as “Ali”. Interestingly, a radio program participant said that it would not have been possible for the Syrian Electronic Army to do whatever it has done had Syria not lifted the ban on Facebook. He added that had Syria lifted the ban earlier, the electronic achievements would have been much greater. Facebook and YouTube had been blocked in Syria for years until Syrian censors lifted the ban on them in February 2011.
On the other hand, the Army has started to archive on its website selected regional and international media coverage and mentions of its activities, and selectively translates the articles into Arabic. Its reporting on the media coverage is celebratory and is presented as a success story. The translations leave out sections of the articles that are critical of the regime.
In addition, the Army has created a special Facebook page (http://facebook.com/ses.news) to cover news of and about the Army.
Attacks on the Syrian Electronic Army
Apparently, members of the Syrian Electronic Army Facebook page have been victims of privacy infringement attempts. The Army’s website said members of its group and its supporters reported that their Facebook accounts had been compromised by “people who do not want good for Syria,” a reference to pro-revolution activists. As a result, the Army started publishing computer security lessons educating their supporters about how to protect and strengthen the security of their Facebook accounts and Internet accounts in general.
Conclusion
What are the broader implications of the Syrian Army attacks? This case is important because pro-government offensive computer network attacks in the Middle East and North Africa, such as these, are likely to grow and become more organized to counter the increasingly sophisticated use of the Internet by political reformers and oppositional groups. The limited success of legal and technical Internet censorship methods to stem the dissemination of political opposition content to and from these countries may encourage the government and its networks of sympathizers to employ more aggressive methods to not just silence their opponents but also attempt to manipulate their content online. Interestingly, we are witnessing more governments using once-vilified social networking and video sharing websites as tools to promote their agendas and influence conflicts in the idea-sphere.
The Syrian army case also underscores the challenges for researchers of distinguishing between the spontaneous actions of groups of citizens supporting regimes out of their own volition, and those actions which are directed, either formally or informally, by governments. Though we believe that more regimes will employ offensive computer network attacks, we also believe that they will try to disguise such efforts and distance themselves out of fear of consequential legal responsibility. Although there are some intriguing connections between the Syrian government and the groups involved in these attacks, we could not find credible evidence that links the two directly beyond the tacit support that would be required for such a group to operate on Syrian networks.
- 1. For example, see the end of this page: http://www.syrian-es.com/component/content/article/72.html (Arabic)



