Unintended Risks and Consequences of Circumvention Technologies: The IBB's
Anonymizer Service in Iran
OpenNet Initiative Advisory 001
Last modified: May 5, 2004
<http://www.opennetinitiative.net/advisories/001/>
I. Executive Summary
Internet access in Iran is subject to official censorship. Iranian authorities'
guidelines for ISPs and users reportedly warn them to avoid all content seen
as being in breach of social and cultural norms.[1] In practice, the filtering of Iranian ISPs extends
to cover political as well as
pornographic web sites.[2] In September 2003, the U.S. International
Broadcasting Bureau (IBB) sponsored the launch of a service through Anonymizer,
Inc., designed to allow Iranian Internet users to bypass much of Iran's national
filtering regime. Throughout this report we refer to the service as the "IBB
Anonymizer" to emphasize that it is distinct from the general services offered
to the public by Anonymizer, Inc.[3]
In December 2003 and April 2004, we ran a series of tests to gauge the accessibility
of sites through the IBB Anonymizer service. We found that many web sites blocked
by Iranian ISPs could be successfully accessed through the IBB Anonymizer service.
However, filters built in to the IBB Anonymizer service, intended to prevent
Iranians from using it to view pornographic sites, also have the unintended
consequence of blocking access to numerous non-pornographic pages and sites.
At fault appears to be the IBB Anonymizer's unreleased list of automated "trigger"
keywords applied to domain names before any pages are shown to IBB Anonymizer
users. These "trigger" keywords appear to generate a significant number of false-positive
results, resulting in a significant amount of collateral blocking -- "overblocking"
-- of non-pornographic sites. For example, the IBB Anonymizer service blocks
non-pornographic websites dealing with women's health issues because the keyword
"breast" is within their domain names. Likewise blocked is the anchor page
for links to the U.S. Department of State's overseas missions -- usembassy.state.gov
-- because it contains the trigger keyword "ass." The service also blocks almost
any site containing the word "asian" in the domain. Some of these apparently
unintentionally blocked sites are themselves blocked within Iran, resulting
in a situation where sites are effectively doubly blocked --by Iranian ISPs and
by the IBB Anonymizer service.
The IBB and Anonymizer Inc. confirmed in separate e-mail exchanges with ONI
researchers that the circumvention service is explicitly configured to block
pornography.[4] They explained that this is intended to
conserve available bandwidth and ensure availability of the service to Iranians
who wish to visit non-pornographic sites. Several notable studies
have pointed out the difficulty of implementing keyword-based filtering systems
in such a way as to avoid the unintended consequence of "collaterally blocking"
non-pornographic sites. The keyword rules that drive the filters built in to
the IBB Anonymizer service are not publicly known, making independent assessment
of those rules and their implications more difficult. (Staff at Anonymizer,
Inc., have declined to publicly disclose keywords or methods, considering them
to be proprietary to the company.)
Further, despite IBB Anonymizer assurances that its Iranian users may surf
the Web freely and safely, our testing suggests that the vast majority of its
traffic is exposed to monitoring by Iranian authorities and corresponding local
ISPs. Iranian users may not be aware that their use of the service may identify
them to Iranian government authorities as citizens wishing to view forbidden
content, or as supportive of the ideas found within that content.
Examples of filtered web sites
The following list contains examples of non-pornographic web sites filtered
on the IBB Anonymizer service, apparently because their domains contain banned
keywords; a lengthier list of apparent overblockages is reproduced further below.
Filtered web sites include those having to do with women's health issues, the
President of the United States, a variety of NGO's, and popular hotel, email,
and other commercial services. In addition, it appears that all domains
registered in Malaysia (.my) and Tuvalu (.tv, popular domain suffix for television-related
material) are blocked.
II. The IBB Anonymizer Service
In response to the recent implementation of Internet content filtering in
Iran, the United States, through its federally chartered International Broadcasting
Bureau, contracted with Anonymizer, Inc. to provide what is known as "circumvention
technology" and services to Iranian citizens. Circumvention
technologies assist Internet users in bypassing content filtering and surveillance
in areas where such practices exist.
Anonymizer, Inc.'s flagship public Anonymizer
service is often adopted for filtering circumvention purposes. While offered
primarily as a service allowing Internet users to visit web sites without disclosing
any potentially identifying information to those operating the site, the basic
Anonymizer technology can also prove useful to those seeking to circumvent certain
kinds of web filtering. Anonymizer works by serving as an intermediary between
the user and the user's desired web site -- a so-called "web proxy service."
By acting as a proxy, only Anonymizer knows a user's IP address -- the visited
site views the visit as coming from Anonymizer's servers rather than the user,
and Anonymizer relays what it views on the site back to the requesting user.
Thus, users prevented from accessing Internet content directly on a site can
seek to connect to the Anonymizer service, which retrieves and relays the content
instead. (For this reason, filtering regimes often filter access to Anonymizer
itself.)
The IBB Anonymizer service is a modified version of the Anonymizer service
offered solely to Iranian Internet users, in conjunction with the Voice of America's
(VOA) Persian Service and Radio Farda. It appears to be materially less
secure than the fee-charging Anonymizer services offered to the public at large
-- its paid encrypted service
and SSH tunneling service.
Operators of web sites visited by users of the IBB Anonymizer will still see
the visits as coming from Anonymizer's servers rather than somewhere in Iran,
but the traffic between IBB Anonymizer and its Iranian users is apparently itself
exposed to network monitoring by Iranian ISPs.
Users that IBB Anonymizer determines to be outside of Iran are unable to access
the service. For those who are found to be within Iran, the service is freely
accessible through several domain names. As soon as the Iranian authorities
block one of the service's domain names or IP addresses, new locations are announced
to Iranians through Radio Farda and VOA Persian Radio broadcasts. (Some of these
domain names are filtered by some ISPs in Iran and thus inaccessible to users, however even
the filtered domains can be accessed by directly entering the IP address.) [5]
As has been reported
elsewhere, pornography filters are present on the IBB Anonymizer service
to prevent Iranians from using the service to retrieve pornographic content.
After media reports indicating that the IBB had procured the services of Anonymizer
Inc. to develop and deploy circumvention technology for Iranian Internet users,
and that the service was configured with pornography filters, we connected to
the IBB Anonymizer services through remote computers located in Iran and sought
to determine how well the system worked, and what sorts of sites the system
itself filtered.
A. How the IBB Anonymizer works
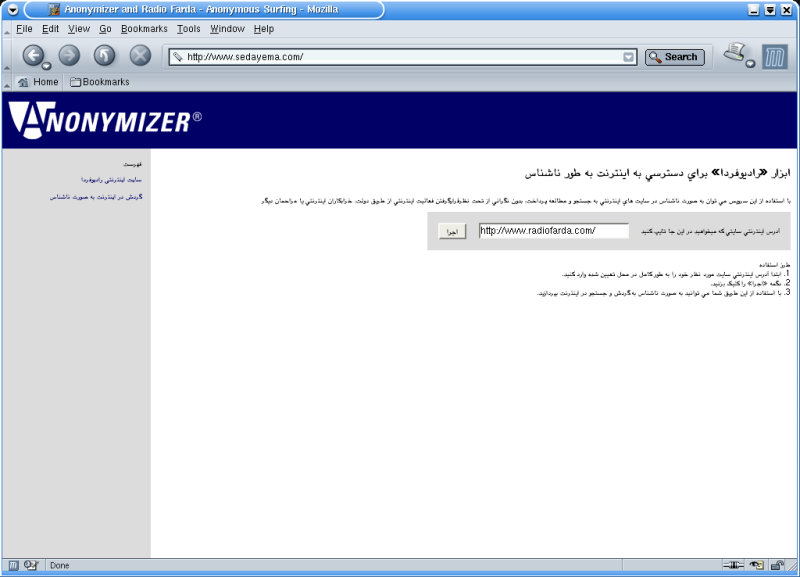
1. When accessing the IBB Anonymizer, users are presented with a web form into
which URL's can be entered:
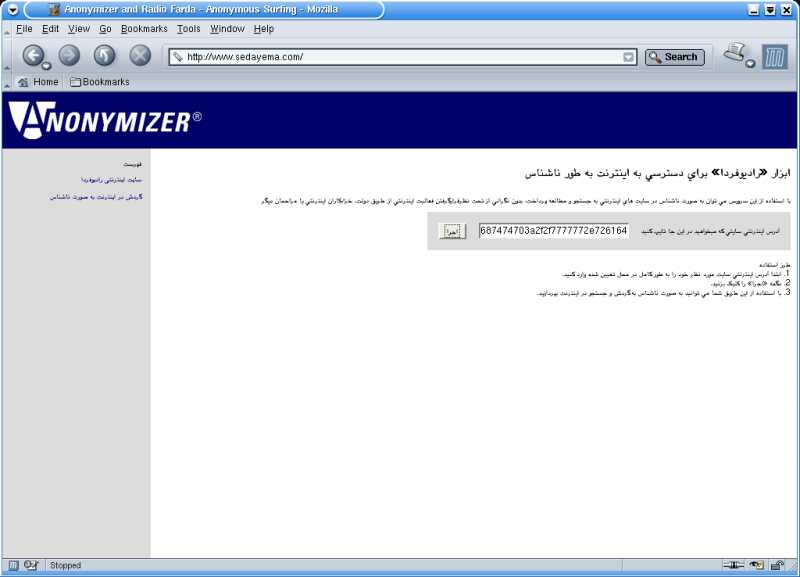
2. The requested URL is obfuscated within the user's browser, but not formally
encrypted, by converting the ASCII text to hexadecimal using JavaScript.
In this case, http://www.radiofarda.com/ becomes...
687474703a2f2f7777772e726164696f66617264612e636f6d2f
The conversion of ASCII text to hexadecimal might render the submission of
the requested URL to the IBB Anonymizer more subtle -- since URL keyword scanning
by the Iranian authorities, if present, would possibly expect plain text rather
than hexadecimal -- but it would be an easy technical adjustment for anyone
surveilling the exchange to convert hexadecimally encoded URLs back into ASCII.
Thus it's not clear why URL obfuscation takes place at all.
3. The request is transported over HTTP, using POST, to a CGI script that processes
and redirects the request.
POST http://sedayema.com/jump.cgi HTTP/1.1
url=687474703a2f2f7777772e726164696f66617264612e636f6d2f&k=&manual=yes&onclick%3D%27xorValue%28document.menu.url.value%2Cdocument.menu.k.value%29%27=%D8%A7%D8%AC%D8%B1%D8%A7
Location: http://anon.barandaz.com/cgi-bin/redirect.cgi?url=687474703a2f2f7777772e726164696f66617264612e636f6d2f
After setting some preferences via a cookie, the request is then redirected once
again.
Location: http://util.barandaz.com/cgi-bin/action.cgi?url=687474703a2f2f7777772e726164696f66617264612e636f6d2f&go=go
The requested URL is then encrypted
using the Blowfish algorithm,
redirected once again where a GET request is issued for the URL.
Location: http://anon.user.barandaz.com/cipher:pEtUzcn+vRTQ+kAURpvqhOt4d3DZ/FkLutmGdOovcmLYzNbqUtINeQ==:
GET http://anon.user.barandaz.com/cipher:pEtUzcn+vRTQ+kAURpvqhOt4d3DZ/FkLutmGdOovcmLYzNbqUtINeQ==: HTTP/1.1
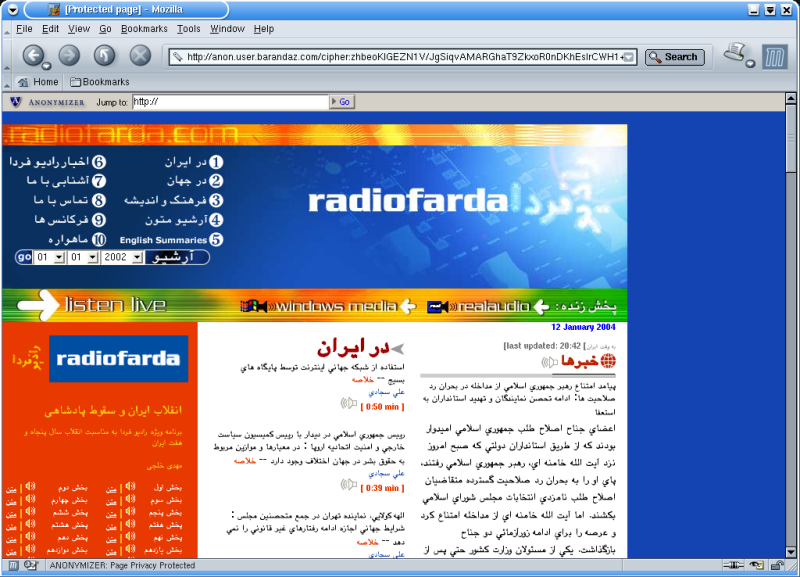
The IBB Anonymizer retrieves the requested content and displays it to the user.
All links within the requested content are re-written to point through the IBB
Anonymizer proxy so that the end-user can browse the Web seamlessly -- a Web page
that might link to www.cnn.com instead will be found by the user to link to a
request for cnn.com through the IBB Anonymizer system, so that browsing
links in displayed pages can continue through the IBB Anonymizer. The use of the
well-regarded Blowfish algorithm to encrypt the user's requested url in the second
round seems puzzling, since the URL is sent encoded to the IBB Anonymizer
service in the first instance.
B. IBB Anonymizer-Filtered Content
Our testing shows that the IBB Anonymizer service provides nearly unlimited access
to the entire Web, including content filtered by many Iranian ISPs. As previously
reported, however, this service is configured to prevent use of its system to
obtain sites with sexually-explicit content. In particular, our testing indicates
that web hosts with certain keywords in their domain names are unavailable for
circumvention. The impermissible keywords generally refer to sexually-explicit
English content including the words "ass," "breast," "naked," and "sex," though
some -- such as "my" -- do not. Domain names containing such keywords
anywhere within are unavailable through IBB Anonymizer, though if the keyword
is found within a directory embedded in the URL (such as "www.name.com/ass"),
it does not trigger filtering.
For example, when a request is issued for http://www.playboy.com, the
requested URL is obfuscated by converting the ASCII text to hexadecimal using
JavaScript. http://www.playboy.com becomes:
687474703a2f2f7777772e706c6179626f792e636f6d2f
The requested is transported over HTTP, using POST, to a CGI script that processes the request and redirects the request.
POST http://sedayema.com/jump.cgi HTTP/1.1
url=687474703a2f2f7777772e706c6179626f792e636f6d2f&k=&manual=yes&onclick%3D%27xorValue%28document.menu.url.value%2Cdocument.menu.k.value%29%27=%D8%A7%D8%AC%D8%B1%D8%A7
Location: http://anon.barandaz.com/cgi-bin/redirect.cgi?url=687474703a2f2f7777772e706c6179626f792e636f6d2f
After setting some preferences via a cookie, the request is then redirected once
again.
Location: http://util.barandaz.com/cgi-bin/action.cgi?url=687474703a2f2f7777772e706c6179626f792e636f6d2f&go=go
The requested URL is then encrypted using the Blowfish algorithm, redirected once
again where a GET request is issued for the URL.
Location: http://anon.user.barandaz.com/cipher:B3EoSzC2Kmgvv2R2Z3JtFx/aI9nzBi2IEGWPI+teMBZKGyCaP5unuQ==:
GET http://anon.user.barandaz.com/cipher:B3EoSzC2Kmgvv2R2Z3JtFx/aI9nzBi2IEGWPI+teMBZKGyCaP5unuQ==: HTTP/1.1
Instead of retrieving the requested content and displaying it to the user, the
request is redirected to a block page of some sort, but the block page itself
appears to be unavailable:
HTTP/1.1 302 Moved Temporarily
Location: https://ssl.kuaidiannao.com/blockpage.html
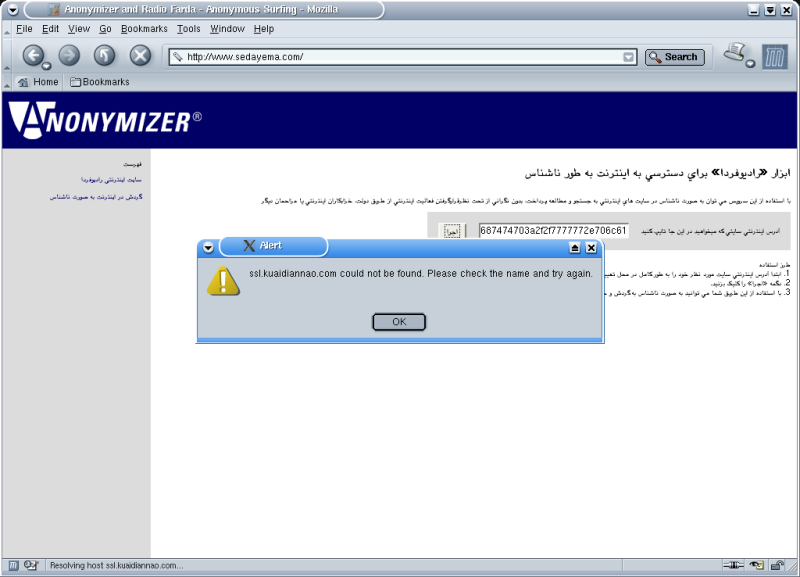
The site to which users are redirected when accessing banned content (ssl.kuaidiannao.com)
was not accessible.
In the case above, "playboy.com" appears to be blocked because it
contains the word "boy" -- indeed, any domain name containing "boy"
is blocked.
Due to these rules, many sexually-explicit sites are indeed unavailable. But
other sites are unavailable too, for words like "ass" appear in the host names
of numerous sites not providing sexually-explicit content. For example, usembassy.state.gov
is unavailable due to the presence of the letters "ass" within the server's
host name, and sussex.police.uk is unavailable for the same reason. In addition,
the words "my" and "tv", which are also domain suffixes, are filtered by IBB
Anonymizer. As a consequence, all web hosts registered within the domain name
systems of Malaysia and Tuvalu are unavailable. Such content can still be accessed
by directly entering the IP address of a particular domain, thus bypassing the
domain name keyword filtering, but many Internet users do not have the technical
ability to determine the IP address of a blocked domain name.
Manual testing revealed that when specific substrings or groups of letters
(usually with pornographic connotations) that appear within standard words,
were found within a domain name, that web host was inaccessible through the
IBB Anonymizer service. Along with manually chosen words (such as "playboy"
from "boy"), we used Princeton's WordNet
lexical database to generate a set of larger words containing apparently-banned
substrings. Each of these words was then used as search terms in a standard
Google search to generate lists of non-pornographic
URLs. We ran each search with Google's inurl:
modifier to generate a list of highly ranked domain names with the specified
keyword in the domain as well as any directory or filenames within the URLs.
Finally, we scrubbed the Google results to include only domains that contain
the relevant keyword, as the IBB Anonymizer does not filter URL paths beyond
the domain name that contain the banned keywords.
When we ran the Google searches we asked for Google's "safe
search" to be on, thus generating search results that were not deemed
by Google's automated system to be pornographic. Of course, Google is not 100%
effective in screening out all pornographic content, and so some of the results
below contain pornographic web sites.
List of blacklisted keywords
Each of the domains was accessed through five remote computers located in
Iran and through IBB Anonymizer. The results show that domains with these
substrings are being blocked with IBB Anonymizer.
Complete test results -- a master list,
indexed by banned substring keyword, of all the domains (and corresponding web
sites) we found to be blocked by IBB Anonymizer.
Whitelisted Domains
While the rules determining the IBB Anonymizer's web blocks appear quite
simple -- whether or not a domain name contains a certain keyword -- there
appear to be some manually-inserted exceptions. Some specific domains as well
as many domains that contain the .us domain suffix have been placed on a whitelist
- accessible despite containing blacklisted keywords. Examples include: chat.yahoo.com,
chat.lycos.nl, www.breast--enlargement.us and www.asian-singles.us.
Whitelisted domains
"Double Blocked" Sites
IBB Anonymizer's filtering may have little effect on Iranian web surfers,
for users can often request the corresponding sites directly through their
Iranian ISPs without using IBB Anonymizer. But Iranian users have no such
option for sites that are blocked both by Iran and by the IBB Anonymizer.
We thus sought to discover a set of such sites.
The results below show sites blocked by both the IBB Anonymizer service and
Iran, to the extent Iranian filtering can be determined.[2]
�Most appear pornographic, with one significant exception - the site for National
Iranian Television, www.nitv.tv, a self-described independent 24-hour Persian
TV station providing uncensored news, current affairs, political, cultural,
educational and entertainment programming productions. The site is mistakenly
filtered by IBB Anonymizer because of the keyword "tv" in the domain. �Iran
presumably censors the site for political reasons.
Sites filtered both by Iran and by IBB
Anonymizer
C. Security and Privacy Implications of the IBB Anonymizer Service
The IBB Anonymizer service works in a way that leaves major gaps in users'
security and privacy. On the one hand, operators of users' requested web sites
cannot distinguish among IBB Anonymizer users, nor readily identify the true
location or identity of any IBB Anonymizer user visiting their sites unless
the user chooses to fill out a web form or otherwise indicate more about themselves.
Like Anonymizer's main service, IBB Anonymizer provides an increase in privacy
by hiding the users' true identities from web site operators.
However, IBB Anonymizer provides minimal protection against monitoring by
the Iranian users' primary ISPs or the Iranian government. IBB Anonymizer
connections use plain text HTTP, easily monitored via a "packet sniffer" or
other network intermediary device. By analyzing the content of the Web pages
being sent from the IBB Anonymizer to individual users in Iran, Iranian ISPs
can readily determine what Web sites and pages their users visit -- even if
they use IBB Anonymizer. Since the URL is only converted to hexadecimal
it is possible to block, monitor, and/or determine the domain/URL users are
requesting through the service (because a hexadecimal string can be blocked
as easily as a domain). When the domain/URL is finally encrypted with Blowfish
algorithm, the domain/URL is properly protected but the content of the requested
web page is not, and can easily be intercepted.
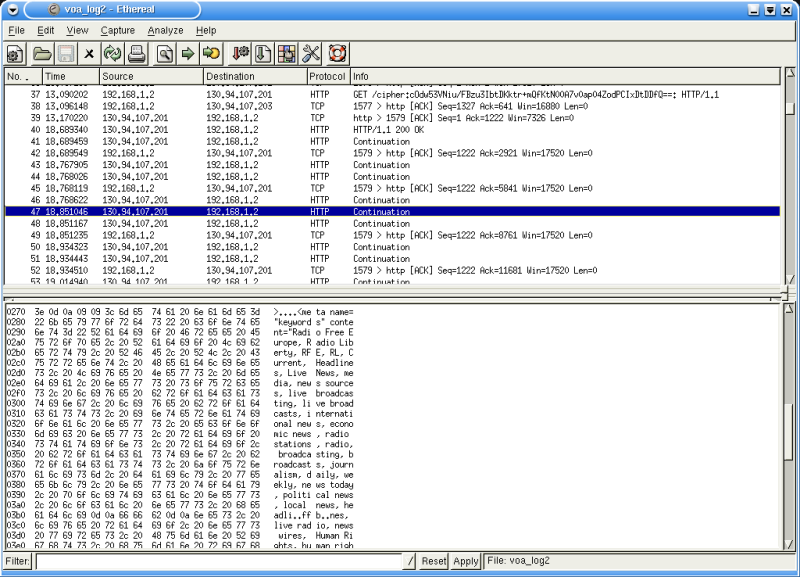
* As illustrated above, the content of www.radiofarda.com can be easily identified
and deciphered by an intermediary even though the user at IP address 192.168.1.2
is connecting through the IBB Anonymizer at 130.94.107.201 to access the Radio
Farda web site.
IBB Anonymizer can therefore leave a user worse off in at least two distinct
respects. First, IBB Anonymizer may tend to call attention to its users who
request the IBB Anonymizer site, facilitating easy monitoring of the users
and their activities. Second, IBB Anonymizer tends to give users a false sense
of security. The IBB Anonymizer service specifically promises:
With this service you can surf, search and read the Internet
anonymously, without the fear of being traced by the government, hackers
or other intruders. [Translated from the text at http://www.sedayema.com]
While Anonymizer does acknowledge the insecurity of the plaintext system
on their public service, nowhere is it acknowledged with respect to the IBB
Anonymizer service -- a striking omission given the "Anonymizer" title for
the service and the fact that users might refrain from using it if they were
aware that web page contents could be readily monitored by the authorities.
�A "premium" version of Anonymizer offered by the company for the worldwide
public offers encrypted communications from start to finish, indicating that
IBB could have contracted with Anonymizer to provide a wholly secure service.
Requests to load a page anonymously are sent by your web browser to our Anonymizer servers.
Unless you are using our SSH Tunneling service, these requests travel over the Internet
"in the clear" (as plain text). Thus, it is possible for your ISP, network administrator,
or other intermediary to easily log the sites that you visit. URL Encryption� prevents this
invasion of privacy by rendering the URLs of the web sites you visit meaningless to outside
observers. [From anonymizer.com]
III. Conclusion
This case study of the IBB Anonymizer service reveals the growing complexity
of censorship and circumvention issues related to the Internet. The very existence
of the service suggests that the United States government has embraced a policy
of facilitating freedom of information in the Middle East and elsewhere, and
this is consistent with the VOA
charter. It is curious to find the United States government promoting
a tool to circumvent Iranian limits on freedom while imposing crude and, even
by its own standards, widely overdrawn limits of its own.
On a more general level, the IBB Anonymizer case raises serious issues concerning
the increasingly widespread practice of content filtering on the Internet.
These include the potential inaccuracy of proprietary and other secretive
filtering mechanisms along with the unintentional problems these can create
for the countries that employ them. There is also the potential risk to users
who think they are using an "anonymous" circumvention technology, which can,
in fact, be traced and tracked. Overall, the case underscores how controls
can be imposed on the physical and operational levels of the Internet, beneath
the immediately apparent interface levels to which most users are accustomed
-- controls that have enormous implications for what can be communicated and
how.
The technical research for this advisory was led by Nart Villeneuve, Director of Technical Research ONI/Citizen Lab, with
the assistance of Michelle Levesque.
About the OpenNet Initiative
The OpenNet Initiative is a partnership among the Citizen Lab at the Munk
Centre for International Studies, University of Toronto, the Berkman Center
for Internet & Society at Harvard Law School, and the Advanced Network Research
Group at the Cambridge Security Programme, University of Cambridge.
We issue reports such as this in response�to topical events, policy debates,
and other issues that call for immediate circulation.�These�complement our
ongoing detailed national and regional filtering and circumvention analyses,
and are designed to provide scholars, policymakers, and other interested parties
with timely access to raw data generated through our technical research.
ONI principals:
Ron Deibert, Director, Citizen
Lab, Munk Centre for International Studies, University of Toronto; r.deibert
at utoronto.ca
Rafal Rohozinski,
Director, Advanced Network Research Group, Cambridge Security Programme, University
of Cambridge; rar20 at cus.cam.ac.uk
Jonathan Zittrain and John
Palfrey, Berkman Center for Internet and Society, Harvard Law School, Harvard
University; zittrain at law.harvard.edu and jpalfrey at law.harvard.edu
* The authors thank Ben
Edelman for comments and contributions to earlier drafts of this advisory,
and Hossein Derakhshan for translations of
Persian.
[1] See, for example, Babak Rahimi, "Cyberdissent:
The Internet in Revolutionary Iran," Middle East Review of International
Affairs, Vol. 7, No. 3 (Sept. 2003).
[2] Determining what content is blocked in a country as
a whole is very complicated; the scope and nature of Iranian filtering -- and
the distinct challenges in measuring it -- will be covered in a separate white
paper.
[3] The IBB is a federal agency of the United States
which includes the Voice of America and
Radio Farda, news and information services
tailored to reach audiences in worldwide, including countries that impose official
censorship. Through an arrangement with Anonymizer, Inc., the IBB has undertaken
to offer a service to Internet users in Iran to bypass that country's Internet
content filtering. Throughout this report we refer to the service as "IBB Anonymizer"
to emphasize that it is distinct from the regular and commercial services offered
by Anonymizer,Inc.
[4] The ONI contacted the International Broadcast Bureau
(IBB) and Anonymizer to ascertain the motivation for configuring the IBB Anonymizer
service with pornographic filters. �The response was that the filters are employed
because allowing access to pornographic data through the service is not a prudent
use of U.S. taxpayer dollars and would create excessive demand on scarce bandwidth,
squeezing out users' ability to access non-pornographic sites. � Email correspondence
with Ken Berman of the IBB on April 7, 2004 and Lance Cottrell of Anonymizer
on April 7 and 14, 2004.
[5] The filtering technology employed by Iranian ISPs
could be configured to block web requests by both domain name and IP address.
This is the case with some domains such as playboy.com, however, additional domains
added to the block list by the Iranian authorities are configured to only block
domain names and not IP addresses. Thus, blocked IBB Anonymizer domains are accessible
by directly entering the IP address.
Filtering Studies
Sites Blocked by Internet Filtering Programs
http://cyber.law.harvard.edu/people/edelman/mul-v-us/
Children's Internet Protection Act
Study of Technology Protection Measures
http://www.ntia.doc.gov/ntiahome/ntiageneral/cipa2003/CIPAreport08142003.pdf
See No Evil: How Internet Filters Affect the Search for Online Health Information
http://www.kaisernetwork.org/health_cast/uploaded_files/Internet_Filtering_exec_summ.pdf
Access Denied: The Impact of Internet Filtering Software on the Lesbian and
Gay Community
http://www.glaad.org/documents/media/AccessDenied2.pdf
Internet Filters: A Public Policy Report
http://www.fepproject.org/policyreports/filteringreport.pdf
Additional resources:
http://peacefire.org/
http://sethf.com/anticensorware/
http://censorware.net/
Anonymizer free trial blocks pages with "young" or "old" in the URL (??)
May 12 2002
By Bennett Haselton (peacefire.org)
Seth Finkelstein has pointed out that Bennett Haselton had previously discovered
that Anonymizer blocks by keyword and that some domains are whitelisted.
Additional Sources:
U.S. Sponsors Anti-Censorship Web Service
By Kevin Poulsen, SecurityFocus Aug 26 2003
http://www.securityfocus.com/news/6807
Anonymizer Makes the Internet a Safer Place for Iranian Citizens
http://www.anonymizer.com/media/releases/030911.html
Anonymizer URL Encryption� FAQ
http://anonymizer.com/docs/faqs/url_encryption.shtml




